Automated IP Reputation Classification
Built an automated workflow that processes firewall IP addresses in controlled batches, classifies them as malicious or clean using reputation intelligence, and prepares results for reporting while respecting API limits and failure conditions.
Read more ▾
How it works
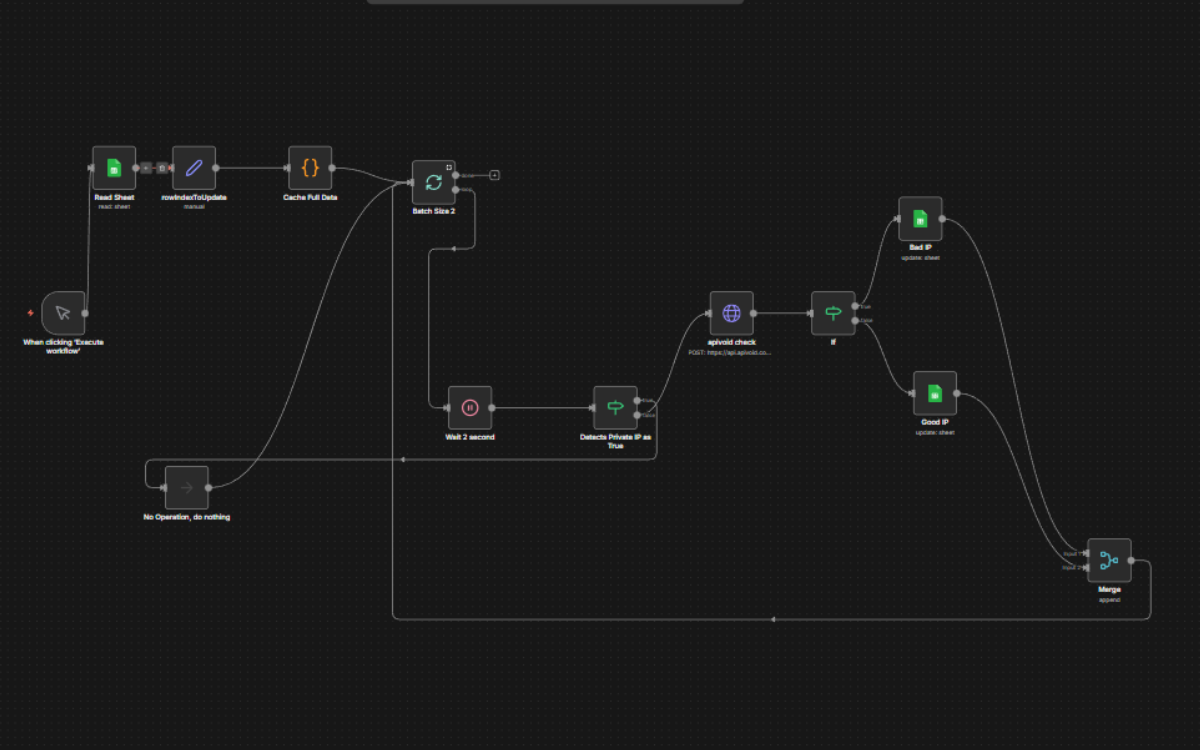
The workflow is designed to safely process large IP datasets under real-world constraints.
IP addresses are read once from a source spreadsheet and cached in memory to minimize repeated reads and avoid quota exhaustion. A batch controller processes two IPs at a time with a timed delay to comply with third-party API rate limits.
Before analysis, each IP passes through a validation gate to detect and skip private or invalid ranges, preventing unnecessary errors. Valid public IPs are sent to an external reputation service for analysis and classified as malicious or clean based on predefined criteria.
Results are merged and returned to the batch controller, allowing the pipeline to continue running regardless of mixed outcomes or partial failures.
Key design considerations
- Rate-limited batch processing
- API quota protection
- Input validation before execution
- Failure-tolerant looping and retry handling
- Continuous execution without hard stops
Outcome
The workflow eliminates manual IP reputation checks, safely processes large datasets, and integrates cleanly into existing reporting workflows. It reduces manual classification effort by approximately 80% while maintaining accuracy and operational stability.

